By David Maidment, Senior Director Secure Device Ecosystem, Arm
The growing popularity and adoption of the Internet of Things (IoT) has highlighted the possibilities of digital transformation. As deployment scales across new markets, we are seeing a rise in the number of insecure devices and, consequently, a rise in the number of cybersecurity attacks. On average there are 5,400 attacks per month on IoT devices and 7 million data records compromised daily. This brings a new and complex set of risks for device manufacturers (OEMs) that impacts their bank balance, damages their reputation and puts a strain on their resources.
Security is non-negotiable and increasingly we are starting to see acknowledgement of the importance of device-level security. However, significant barriers to effective security design and implementation remain, resulting in a slow and fragmented approach across the electronics industry. We must work together to address the challenges of IoT security and unlock the possibilities of a connected future.
The PSA Certified 2021 Security Report surveyed key tech decision-makers from across the world to gather an up-to-date pulse point on the realities of IoT security. With insights from start-ups to multinational organizations, the study takes a comprehensive look at the attitudes, practices, and pitfalls of IoT security.
While the technology industry has made tremendous progress, the report highlighted that there is still work to do. We identified a worrying gap between respondents’ perception of security and reality: where 87 percent said they were satisfied with the quality of IoT security implementations within their company, yet only 47 percent of the same group are carrying out a threat analysis during the design process of new products. To bridge some of these gaps, we need to establish a better understanding of the challenges that OEMs are facing. In this blog, I wanted to share six key challenges we identified in our research and key steps on how you can overcome them.
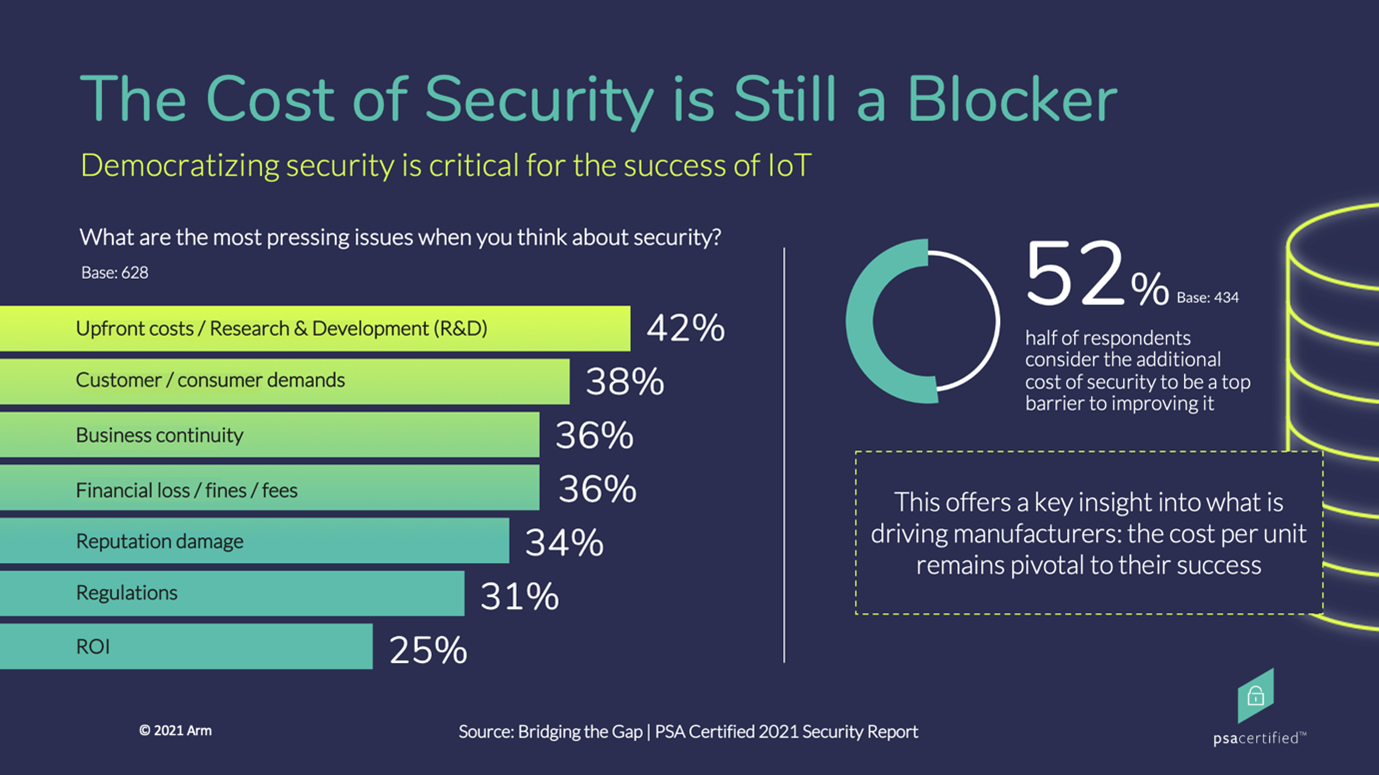
Challenge #1: Reducing the Cost of Security
“Security is just a cost” is something we’ve heard for a long time, and it was heavily mentioned in our report, with 52 percent of respondents noting the additional cost of security as the main barrier to improvement. It’s no surprise that cost is such a concern for OEMs, as device manufacturers need to create a device and sell it for profit – meaning they have to closely manage the cost per unit associated with a device. It’s no secret that every moment spent designing with security in mind comes at a cost, however, it’s important that we look at protection through a different lens. We need to remember that the cost of security is vastly outweighed by the cost of insecurity, both financially and reputationally.
What you can do: Adopt comprehensive frameworks and a common approach to security, which can help reduce the costs associated and speed time-to-market.
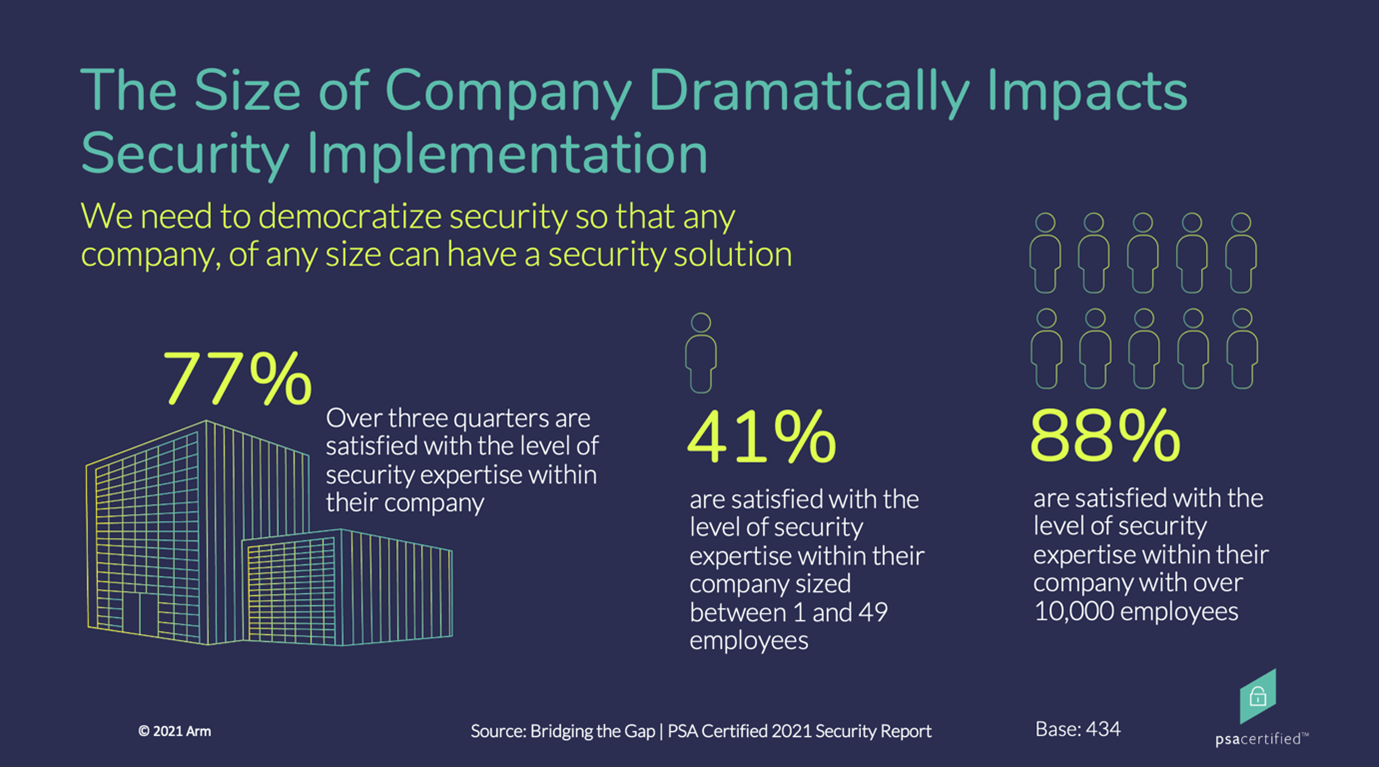
Challenge #2: Gaining Security of Expertise
The issue of cost is exacerbated by a lack of understanding and expertise around security. Forty-two percent of OEMs identified this as one of the biggest IoT security challenges. Overall, 77 percent of respondents were happy with the security expertise in their companies, but unsurprisingly, this problem gets worse in smaller companies where the percentage drops to 41 percent. Small companies often lack the manpower, capital and resources to implement best practices.
What you can do: It’s clear that the industry needs to work together to democratize security properly. If we are to build trust in the IoT, good practice needs to be accessible to all companies regardless of their size.
Challenge #3: Skipping Threat Modeling
The perceived additional cost of security paired with a lack of expertise is resulting in key tasks being completed poorly or skipped altogether. The most alarming of these is the lack of threat modeling adoption: Only 47 percent of respondents are carrying out a threat analysis for every new product and this drops significantly to just 33 percent in smaller companies. Threat modeling is a critical component of security design – if you don’t know what you’re protecting against, how do you know what level of security you need?
What you can do: Working from templates and receiving training or guidance in this area will help combat this challenge and allow OEMs to implement successful threat modeling in the design of each new product.

Challenge #4: Navigating Regulatory Fragmentation
Almost half of respondents also considered the fragmentations of standards and regulations as a key challenge. Across all geographies, governments and regulators are releasing new standards to help combat the number of insecure devices flooding the market. Major examples include the ETSI EN 303 645 requirements in Europe and the NIST 8259A standard in the US. Although three in four tech decision-makers think governments should play a part in a guideline-development process, it still takes a lot of time and resources to evaluate the different IoT security approaches and solutions for OEMs.
What you can do: Look to adopt a common language and unified approach to navigating regulations. Many certifications (including PSA Certified) are starting to map their requirements to upcoming regulations, bridging this gap and easing the security journey for device manufacturers.

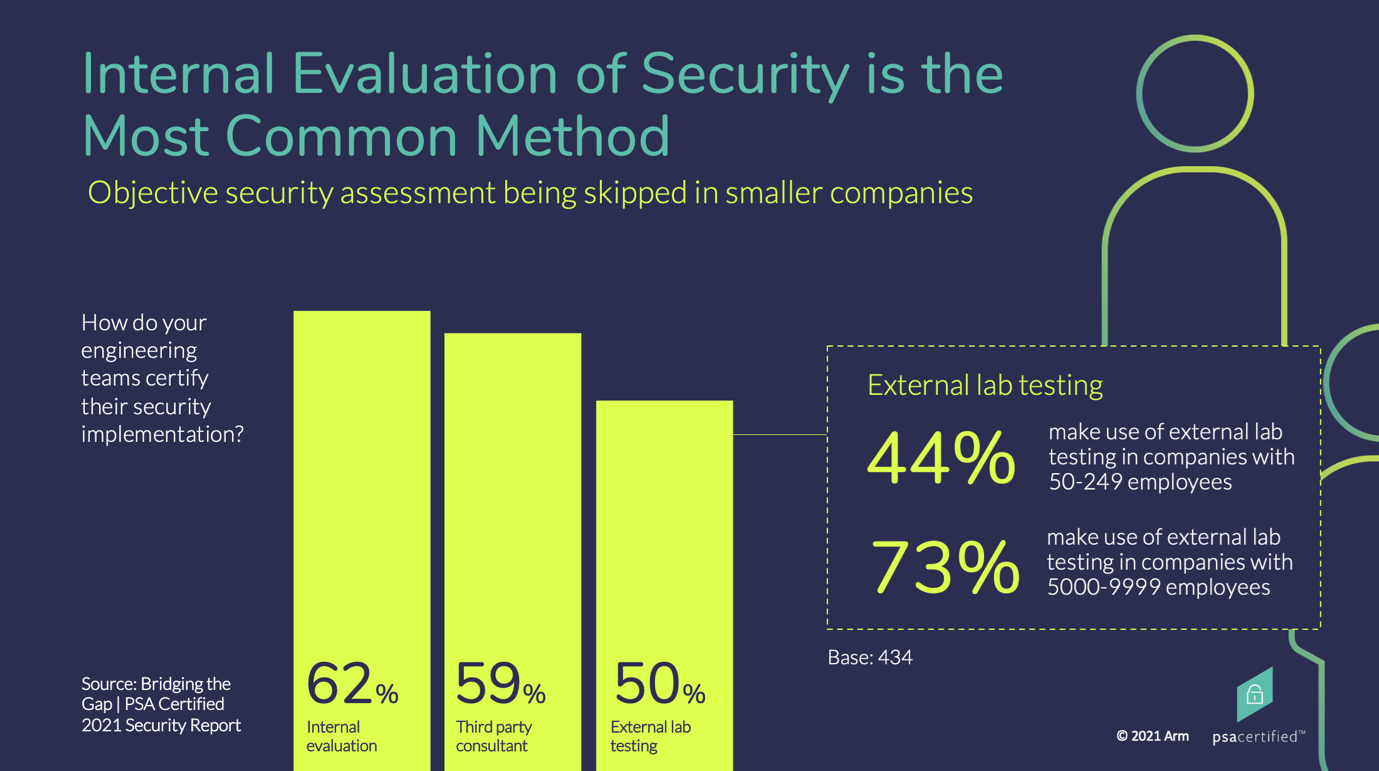
Challenge #5: Validating Security Implementation Internally
The 2021 Security Report also found that 62 percent of engineering teams are internally evaluating their security implementations. Again, company size has a significant impact: Just 44 percent of small to medium-sized businesses are making use of external lab testing, compared to 73 percent of large companies. This is concerning as we need to ensure that we are measuring the robustness of security without any bias. Third-party evaluation and certification should be the preferred approach as it provides an independent assessment of a product’s conformance to industry best practice and offers the industry a way to benchmark their security implementations.
What you can do: Complete a certification scheme that utilizes independent lab-based testing of your product to showcase your commitment to best practice security and build trust in your devices.
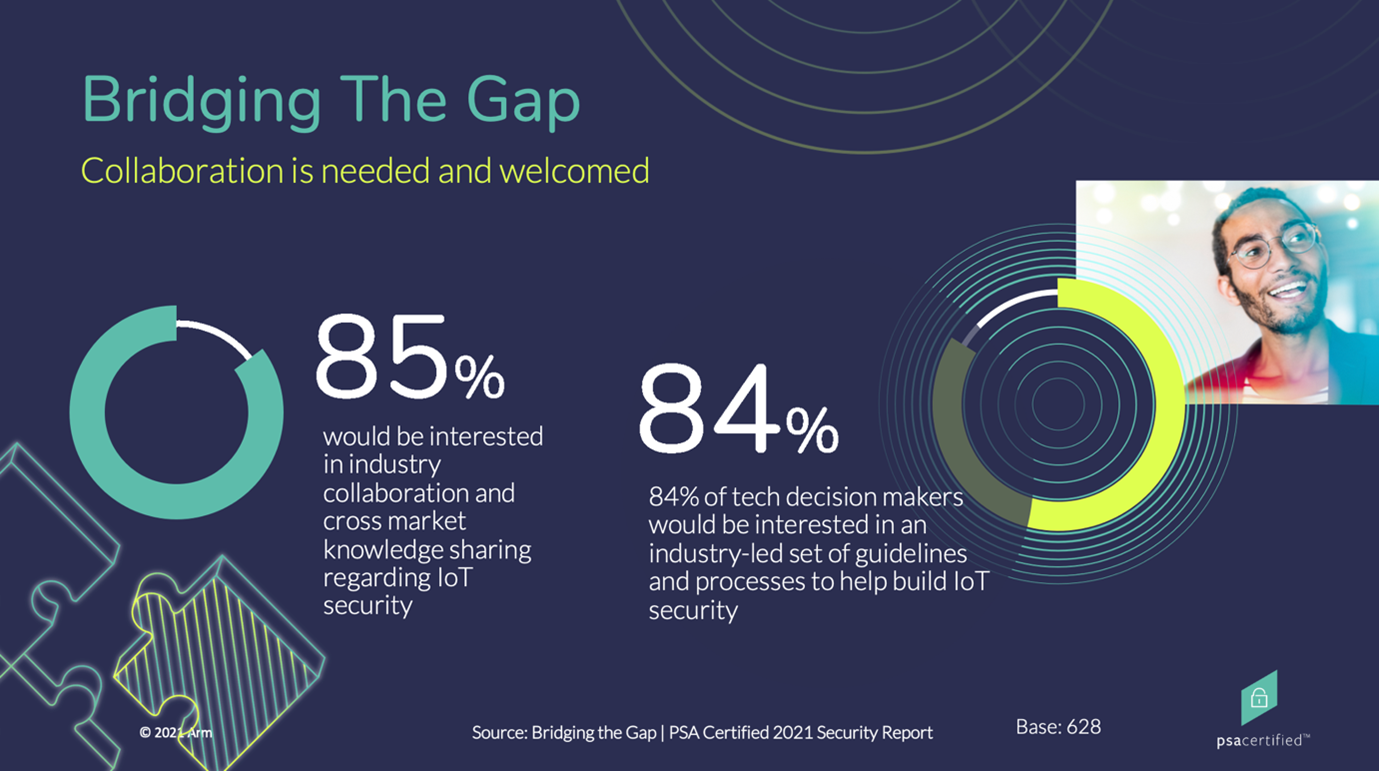
Challenge #6: No Single Company Can Influence the Full Value Chain
The barriers to successful IoT security design and implementation are significant and not something one company or organization can tackle alone. Industry collaboration is paramount and the only way we can develop a unified approach to security that will combat these challenges and bridge the gap. This attitude is reflected by our respondents with 85 percent showing an interest in industry collaboration and cross-market knowledge sharing. This desire from the different members of the value chain to navigate the complexities of IoT security together reduces the burden on OEMs and helps combat issues of cost and a lack of expertise.
What you can do: Initiatives such as The Cybersecurity Tech Accord are helping to foster this collaboration by bringing together leaders from across the tech industry. A founding aim of the Cyber Tech Accord is to “Provide their customers, users and the developer ecosystem with information and tools that enable them to understand current and future threats and better protect themselves.” At Arm and PSA Certified, we’re big believers in this mission and work to bring the ecosystem together and inspire real action from OEMs to implement security best practice into their devices.
It’s clear that security isn’t optional as it is key for scaling digital transformation. It’s also something that cannot be an afterthought- it needs to part of a company’s DNA and built into devices at the very beginning. Our report showed that a lot of OEMs (especially newer and smaller companies) find this overwhelming, and don’t have in-house expertise, especially in newer and smaller companies. The good news is that PSA Certified works across the supply chain to make security best practice a reality, collaborating with other partnerships to democratize security so that any company of any size can have a security solution. You can find out more about the PSA Certified ecosystem and how it can help you implement best practice security into your devices on our website.

