A “Zero Trust” cybersecurity model has been one of the most important innovations in organizational risk management in recent years. It constitutes a fundamental shift in mitigating risk, but one that is still not widely adopted or even understood. This is why, throughout Cybersecurity Awareness Month in October, the Cybersecurity Tech Accord will be breaking down the core elements of “Zero Trust” architecture in a new blog series – Never Trust, Always Verify. The series will feature expert voices from across Cybersecurity Tech Accord signatories breaking down what Zero Trust is, what is isn’t, and how to have an informed conversation to ensure your organization is employing best practices for security. The series will include entries on:
- Zero Trust in IT and OT systems – Schneider Electric
- Strong authentication for Zero Trust – Balasys
- Zero Trust access policies – Safe PC Solutions/Safe PC Cloud
- Threats that necessitate Zero Trust – Contrast Security
Madinah S. Ali, President & CEO – Safe PC Solutions/Safe PC Cloud
The Zero Trust Security Model is an approach to the design and implementation of information technology systems. The main concept behind the architecture is de-perimeterization, which refers to the removal of a boundary between an organization and the outside world. While there is no one definition for Zero Trust, as mentioned in the previous blog in this series the United States’ Cybersecurity and Infrastructure Security Agency (CISA) has identified the following Zero Trust principles:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentications and authorizations are dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications, and uses this information to improve its security posture.
One of the most important aspects of Zero Trust Policy is policy based adaptive access, this is where the organization must define acceptable access policies for its resources and enforce them with a consistent security policy engine that provides both governance and insight into variances.
A zero-trust architecture enforces access policies based on context—including the user’s role and location, their device, and the data they are requesting—to block inappropriate access and lateral movement throughout an environment
Adaptive access policies then are the process of using IT policies to allow administrators to control user access to applications, files, and network features based on multiple real-time factors. An Adaptive access policy is more flexible and secure than a legacy approach to perimeter-based networks and is a requirement for the Zero Trust Architecture (ZTA). Organizations utilize adaptive access policies so they can ensure that the right users with the correct device are connecting to the network within a secure manner.
Policy Optimization or Policy Enforcement
Companies determine their business policies at a high level to designate what resources and information employees can and cannot access. Based on these policies, along with the context of the individual request, Zero Trust Architecture (ZTA) permits or denies access to respective applications. In such a system, private applications are not necessarily exposed to the internet, and access is brokered via outbound-only connections, whereas public applications have conditional access.
Consider an employee from the Human Resources (HR) department using a managed device to access confidential employee data. Managed device are laptops, desktops, virtual machines, mobile devices, and other IT infrastructure equipment that is being monitored utilizing endpoint devices and tools. The purpose of remote monitoring of managed devices is to keep devices updated to prevent cyber-attacks. The Zero Trust Architect (ZTA) would allow an employee to access the confidential data since the employee in the HR department is utilizing a managed device which is required by the adaptive access policy.. However, if the employee uses an unmanaged device, full access will not be given. An alternate policy could instead offer access via a remote browser session that streams data as pixels from an isolated session in a containerized environment, but will not allow the data itself to be accessed, downloaded, cached on the device, etc.
ZTA prescribes a granular connection from the entity requesting access to the resource or application for which access is authorized. This is a true zero trust connection. Even if there is a security threat, it is limited to that connection between the specific requesting entity and the application it is accessing, rather than the entire network. This architecture is fully compliant with the tenets defined in the National Institute Standards of Technology (NIST) framework, essential for any security solution to deliver trusted access.
ZTA eliminates the need for complex MPLS networks, complex perimeter-based security system controls, and VPNs – with fast, secure, direct-to-cloud access and secure cloud-to-cloud connectivity that eliminates backhauling, route distribution, and service chaining. Instead of multiple hardware-based or virtual security solutions that are hard to manage and maintain, an integrated zero trust solution secures all internet, SaaS, and private applications with a single, comprehensive platform. ZTA delivers cloud-native, transparent zero trust access – offering seamless user experience, minimized cost and complexity, increased visibility and granular control, and enhanced performance for a modern approach to zero trust security.
The ultimate objective of policy-based access (i.e., policy optimization or policy enforcement) is to enforce policies related to the permissibility and use of data by authenticating the user, location, device, and/or network.
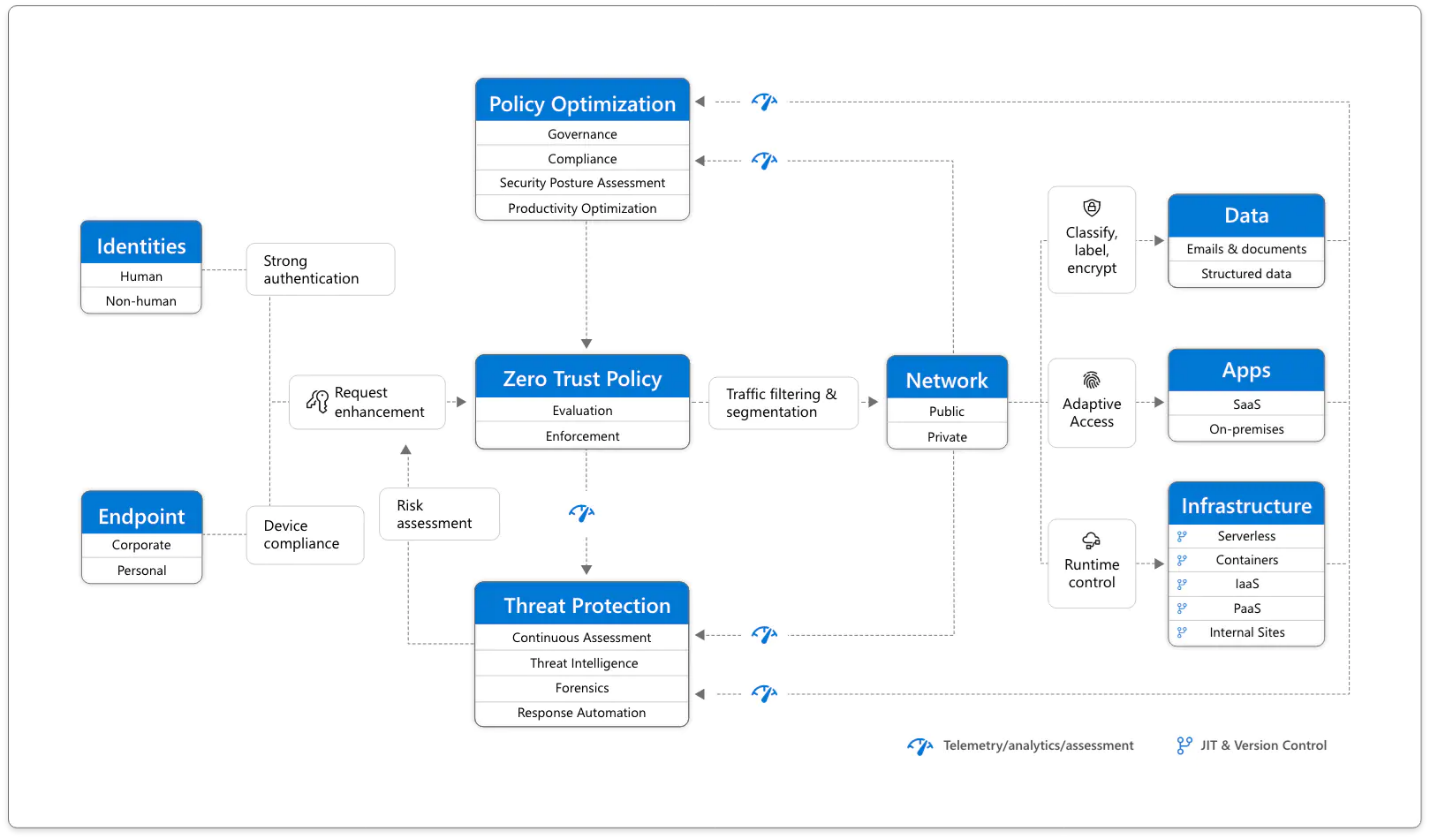
Microsoft Zero Trust Diagram that focuses on Zero Trust Policy. This policy is further enhanced by Policy Optimization. Governance and Compliance are critical to a strong Zero Trust implementation. Security Posture Assessment and Productivity Optimization are necessary to measure the telemetry throughout the services and systems.

